Personal Security Sentinel is a fake security program that performs a fake scan of your computer looking for malicious software and viruses. When the program has finished scanning, it reports false or exaggerated infections on your computer. The rogue program states that malware cannot be removed from your computer using the non-activated copy of Personal Security Sentinel. It's a typical rip-off rogue program. Do not purchase it, that won't help. It's classified as a rogue program and belongs to the FakeVimes family. It's basically the same thing as Internet Antivirus 2011 or My Security Shield. If you have this rogue program on your computer then please follow the removal instructions below to remove Personal Security Sentinel and any related malware from your computer for free using legitimate anti-malware programs.
Image source: rogueantispyware.blogspot.com
Personal Security Sentinel has to be manually installed but if you have a trojan downlaoder on your computer then it can be downloaded onto your computer without your knowledge and permission. It may come from fake online scanners or be offered for download when visiting certain (usually infected) web sites. Once Personal Security Sentinel is installed, it pretends to scan your computer for malware. As a typical rogue, it displays fake security warnings and notifications saying that your computer is infected with spyware, trojans and other malicious software. Furthermore, it modifies Windows Hosts file and hijack Internet Explorer. It enables a proxy server and may redirect you to entirely unrelated websites when you do a search for let's say malware removal tools and etc. Personal Security Sentinel may block other programs on your computer too.
In order to remove Personal Security Sentinel from your computer, you will have to restart your computer in safe mode with networking, disable proxy server and download anti-malware software. Please follow the step by step removal instructions bellow. If you need help removing Personal Security Sentinel malware from your computer, please leave a comment. Good luck and be safe online!
Personal Security Sentinel removal instructions:
1. Reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key. Read more detailed instructions here: http://www.computerhope.com/issues/chsafe.htm
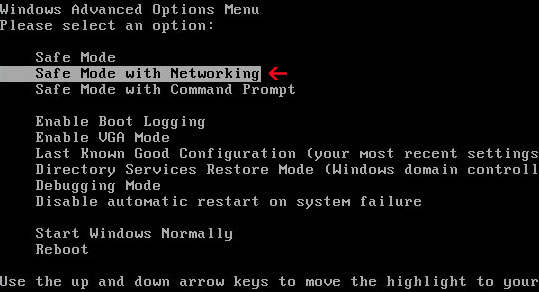
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Launch Internet Explorer. In Internet Explorer go to: Tools->Internet Options->Connections tab. Click Lan Settings button and uncheck the checkbox labeled Use a proxy server for your LAN. Click OK. You may have to repeat steps 1-2 if you will have problems downloading malware removal programs.

3. Download free anti-malware software from the list below and run a full system scan.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
4. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
Personal Security Sentinel associated files and registry values:
Files:
- C:\Documents and Settings\All Users\Application Data\083b\
- C:\Documents and Settings\All Users\Application Data\083b\713.mof
- C:\Documents and Settings\All Users\Application Data\083b\mozcrt19.dll
- C:\Documents and Settings\All Users\Application Data\083b\PersonalSS.exe
- C:\Documents and Settings\All Users\Application Data\083b\PSS.ico
- C:\Documents and Settings\All Users\Application Data\083b\sqlite3.dll
- C:\Documents and Settings\All Users\Application Data\083b\unins000.dat
- C:\Documents and Settings\All Users\Application Data\083b\PSSSys\
- C:\Documents and Settings\All Users\Application Data\095a\Quarantine Items\
- C:\Documents and Settings\All Users\Application Data\PSZJLXVS\
- C:\Documents and Settings\All Users\Application Data\PSZJLXVS\PSLFNABES.cfg
- %UserProfile%\Application Data\Microsoft\Internet Explorer\Quick Launch\Personal Security Sentinel.lnk
- %UserProfile%\Application Data\Personal Security Sentinel\
- %UserProfile%\Application Data\Personal Security Sentinel\cookies.sqlite
- %UserProfile%\Desktop\Personal Security Sentinel.lnk
- %UserProfile%\Desktop\PersonalSS.exe.txt
- %UserProfile%\Start Menu\Personal Security Sentinel.lnk
- %UserProfile%\Start Menu\Programs\Personal Security Sentinel.lnk
C:\Documents and Settings\[UserName]\ (in Windows 2000/XP)
C:\Users\[UserName]\ (in Windows Vista & Windows 7)
Registry values:
- HKEY_CLASSES_ROOT\CLSID\{3F2BBC05-40DF-11D2-9455-00104BC936FF}
- HKEY_CLASSES_ROOT\PersonalSS.DocHostUIHandler
- HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Download "RunInvalidSignatures" = '1'
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "ProxyServer" = "http=127.0.0.1:25553"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Personal Security Sentinel"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\~1.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\~2.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AdwarePrj.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\agent.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AlphaAV "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AlphaAV.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntispywarXP2009.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Anti-Virus Professional.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntiVirus_Pro.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntivirusPlus "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntivirusPlus.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntivirusPro_2010.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntivirusXP "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntivirusXP.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\antivirusxppro2009.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\av360.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\brastk.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Cl.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\csc.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\dop.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\frmwrk32.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\gav.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\gbn976rl.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\homeav2010.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\init32.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MalwareRemoval.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ozn695m5.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pav.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pc.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PC_Antispyware2010.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pctsAuxs.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pctsGui.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pctsSvc.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pctsTray.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pdfndr.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PerAvir.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\personalguard "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\personalguard.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\protector.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\qh.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Quick Heal.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\QuickHealCleaner.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rwg "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rwg.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SafetyKeeper.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Save.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SaveArmor.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SaveDefense.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SaveKeep.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Secure Veteran.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\secureveteran.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Security Center.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SecurityFighter.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\securitysoldier.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\smart.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\smartprotector.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\smrtdefp.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SoftSafeness.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\spywarexpguard.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tapinstall.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TrustWarrior.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tsc.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\W3asbas.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\winav.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\windll32.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\windows Police Pro.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\xp_antispyware.exe "Debugger" = "svchost.exe"
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\xpdeluxe.exe "Debugger" = "svchost.exe"















0 comments:
Post a Comment